AUCTF 2020 - Boom
CTF URL: https://ctf.auburn.eduCategory: Forensics
Challenge description
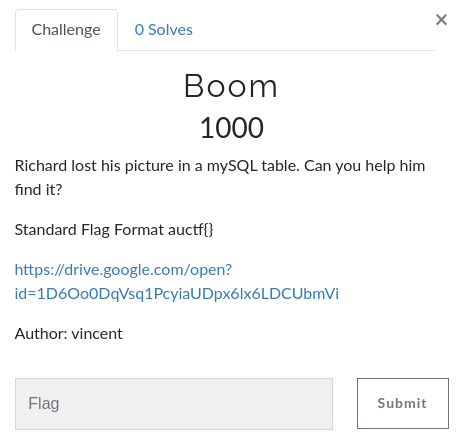
Challenge resolution
For this challenge we were presented with an archive containing an SQL dump file:
-- Adminer 4.7.5 MySQL dump
SET NAMES utf8;
SET time_zone = '+00:00';
SET foreign_key_checks = 0;
SET sql_mode = 'NO_AUTO_VALUE_ON_ZERO';
DROP TABLE IF EXISTS `images`;
CREATE TABLE `images` (
`id` int(11) NOT NULL AUTO_INCREMENT,
`name` varchar(80) NOT NULL,
`image` longblob NOT NULL,
PRIMARY KEY (`id`)
) ENGINE=InnoDB DEFAULT CHARSET=latin1;
INSERT INTO `images` (`id`, `name`, `image`) VALUES
(4, 'hi-res-ba0782735805201b04a654215730b793_crop_exact.7z', '[REDACTED]');
-- 2019-12-03 08:38:34
The [REDACTED] part was the archive in raw format.
Our first attempt was to import the SQL dump to an instance of MySQL.
We then tried to output the contained file using the following SQL query:
select image from images where id=4 into outfile "/tmp/hi-res-ba0782735805201b04a654215730b793_crop_exact.7z";
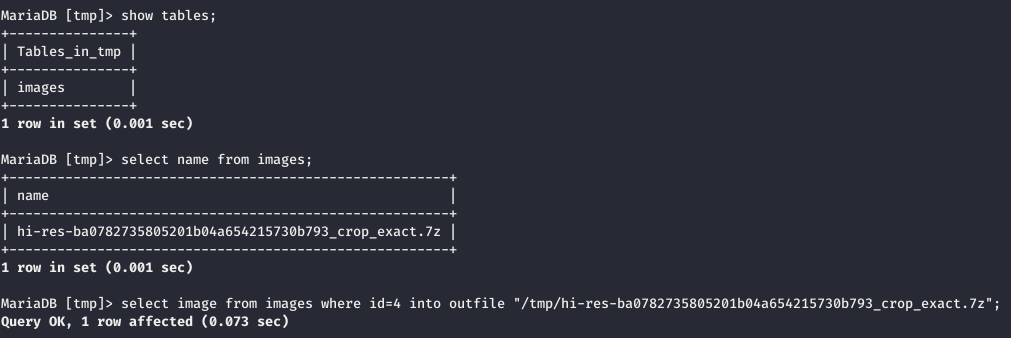
However, the generated file was corrupted.
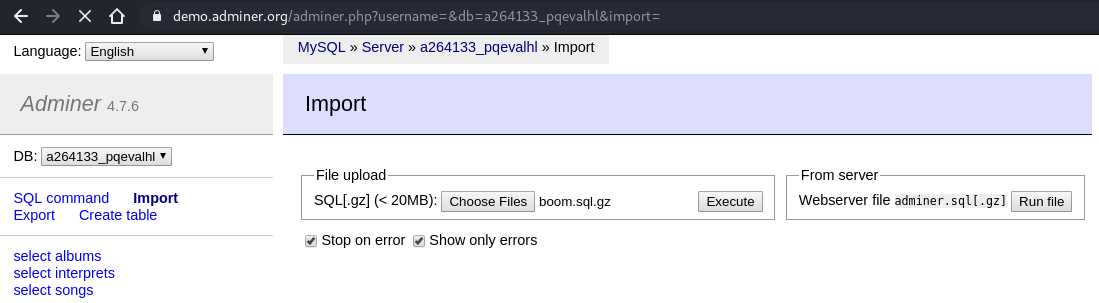
We then looked for the Adminer MySQL dump tool and found an online demo enabling the import of the generated dump file:
From there, we were able to run the SQL query and download the gunzip archive:
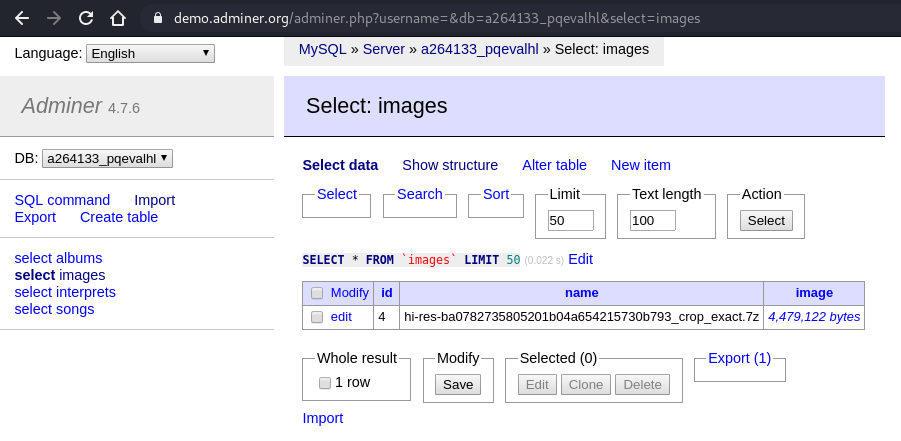
From this archive, we extracted the following picture:

The negative uncovered the flag:

Can you spot it ? It’s right there:

Using some color ajustments finally reavealed the flag:

auctf{B00M_!!}
Author:
@_MrB0b
Post date: 2020-04-06