AUCTF 2020 - Bash {1..5}
CTF URL: https://ctf.auburn.eduCategory: Bash
Challenge description
Bash challenges consisted of a series of linux puzzles reminding us the OverTheWire or Nebula wargames.
Access to each challenge were done via SSH using the flag of the previous level as the password for the next one:
ssh challenges.auctf.com -p 30040 -l level1
Challenges resolution
Level 1
The level 1 was just an intro to show the principle as the flag was stored on the README file:
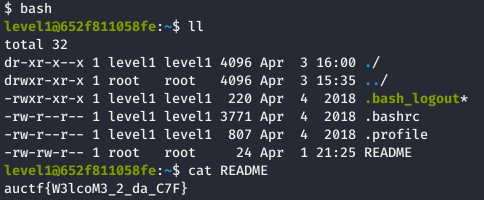
auctf{W3lcoM3_2_da_C7F}
Level 2
For the level 2, the following random_dirs.sh bash script was presented:
#!/bin/bash
x=$RANDOM
base64 flag.txt > /tmp/$x
function finish {
rm /tmp/$x
}
trap finish EXIT
sleep 15
The 15 seconds delay gave us just enough time to consult the latest file created by the level3 user, and stored in the tmp folder:
level2@652f811058fe:/tmp$ cat 21495
YXVjdGZ7ZzB0dEBfbXV2X2Zhczd9Cg==
The base64 decoded output revealed the flag:
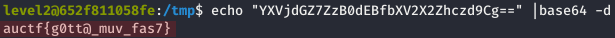
auctf{g0tt@_muv_fas7}
Level 3
The level3’s home folder contained the following files:
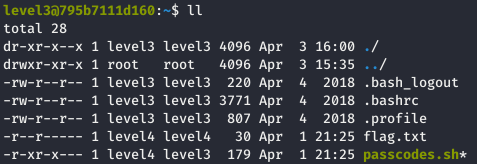
The file we were interested in here was the passcodes.sh bash script:
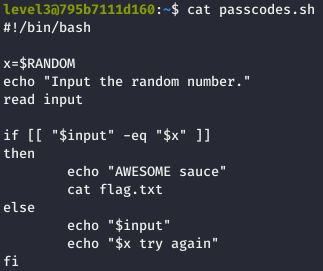
$RANDOM is a bash function that returns a random signed 16 bit integer (from 0 through 32767).
Furthermore, this same script was granted the right to be launched via the sudo command:
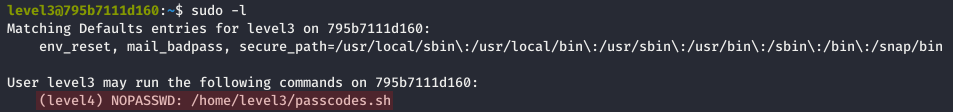
We can thus bruteforce this generated number using the following command in order to retrieved the flag:
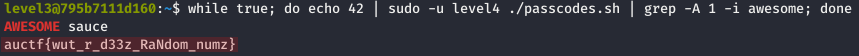
auctf{wut_r_d33z_RaNdom_numz}
Level 4
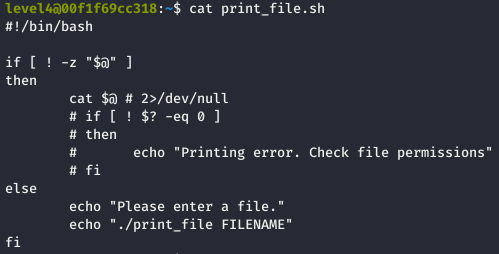
For the level 4, the following print_file.sh bash script was given:
Same as before, the sudo -l command revealed that level4 user can run the print_file.sh script as the user level5:
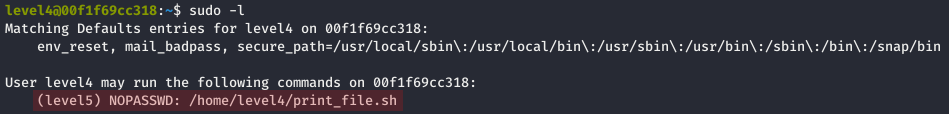
We were thus able to simply retrieve the flag with the sudo -u level5 command:
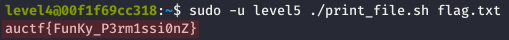
auctf{FunKy_P3rm1ssi0nZ}
Level 5
The final level consisted of the following portforce.sh bash script:
#!/bin/bash
x=$(shuf -i 1024-65500 -n 1)
echo "Guess the listening port"
input=$(nc -lp $x)
echo "That was easy right? :)"
cat flag.txt
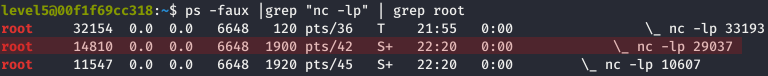
While running the portforce.sh script, the netstat command enabled us to list the latest binded port:
We were finally rewarded with the flag by connecting to the identified port using netcat:
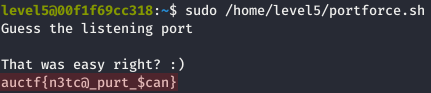
auctf{n3tc@_purt_$can}
Author:
@_MrB0b
Post date: 2020-04-06