Ph0wn 2018 - Track the hacker
CTF URL: http://ph0wn.org/Category: Misc
Challenge description
This challenge was the next step of Save the factory. We were told that the hacker found a way to store data, some kind of file, and we were asked to find it.
Challenge author: m0eukh
Challenge resolution
Like previously, we discovered that many nodes were standing out. They were named frg_<number>, like “fragment number…“.
-
Using the
ualstool: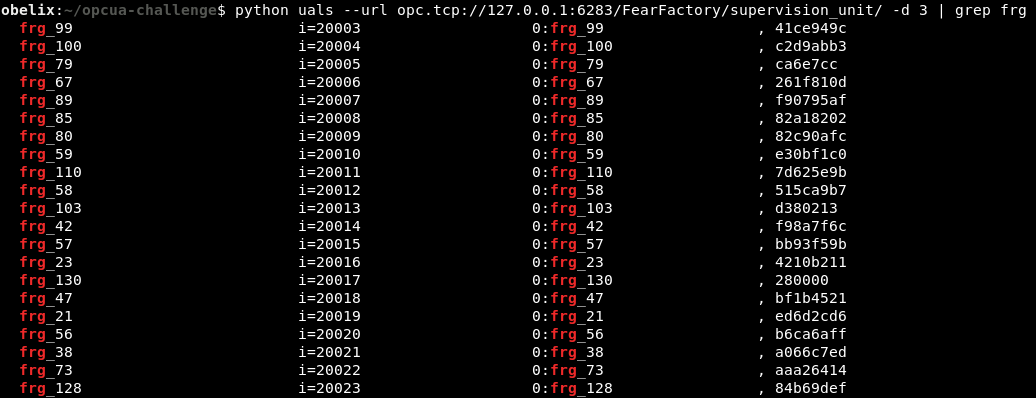
-
Using the provided interactive Python shell:
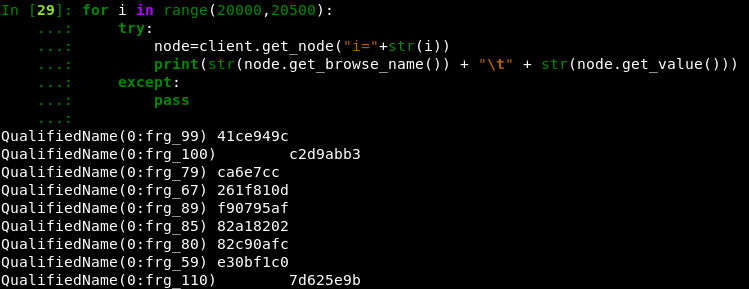
Their values were hex encoded. We retrieved them and sorted the nodes based on the number in their name.
But a simple mistake cost us a lot of time: the leading zeros were missing from the output (i.e. a 2-bytes value 0x0123 would have been displayed 123 with the first 0 missing).
After adding the leading zeros, we concatenated all values (using the Hxd hexadecimal editor on Windows). The file command on the output file looked promising:
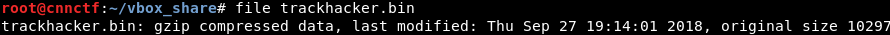
We expanded the file with gunzip and spotted the flag directly in the output:
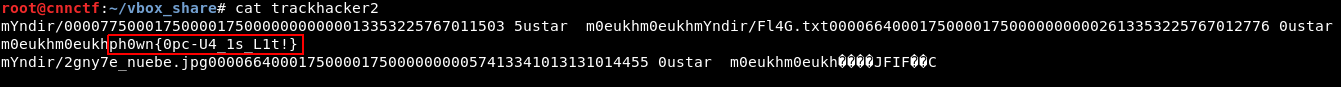
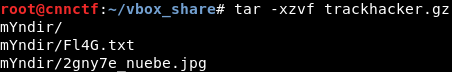
The flag was mixed with garbage since it was actually contained in a Tar archive:
Author:
Clément Notin | @cnotin
Post date: 2018-12-16