Ph0wn 2018 - Save the factory
CTF URL: http://ph0wn.org/Category: Prog
Challenge description
We were provided with information about a factory with machines controlled by a main board that was compromised by an attacker. We were told that the OPC UA machine to machine communication protocol for industrial automation was used. We had SSH access to this main board (Linux based) with an example Python client. The OPC UA server was also directly available via TCP.
Challenge author: m0eukh
Challenge resolution
The provided sample client was based on the python-opcua library. We discovered that this library also provides tools such as uals (tool and implementation).
OPC UA is based on a tree with nodes containing data. The uals tool walks the tree and displays the values.
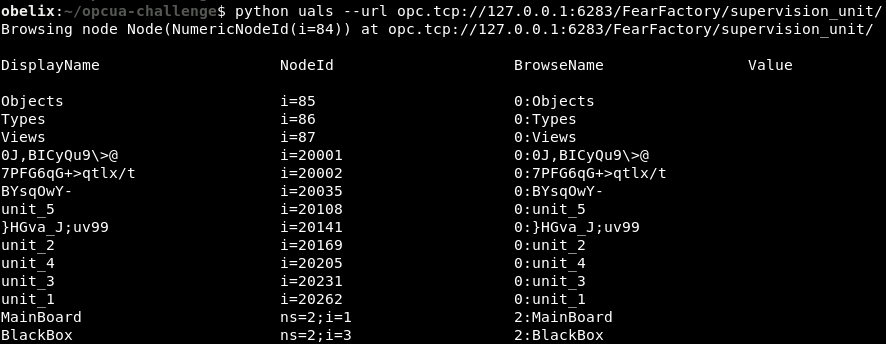
We spot the BlackBox node that was indicated in the challenge description.
We re-launch uals to walks the tree, up to the specified depth (-d 2) and quickly find the flag:
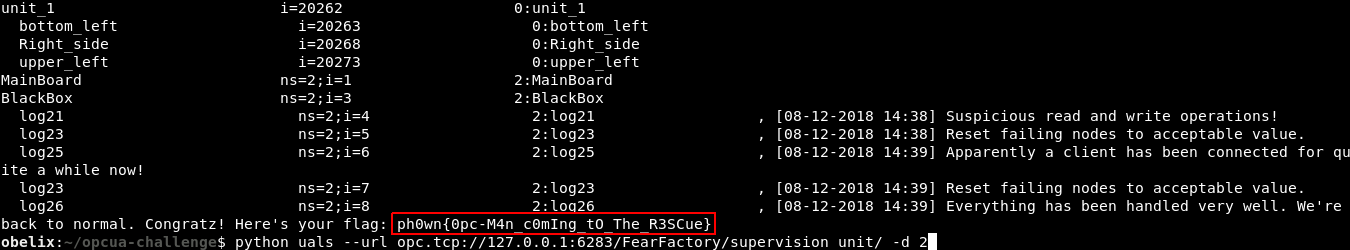
It was certainly not the intended solution, but it worked ![]()
We could also have used a GUI tool such as OPC-UA GUI Client and connect directly via Internet:
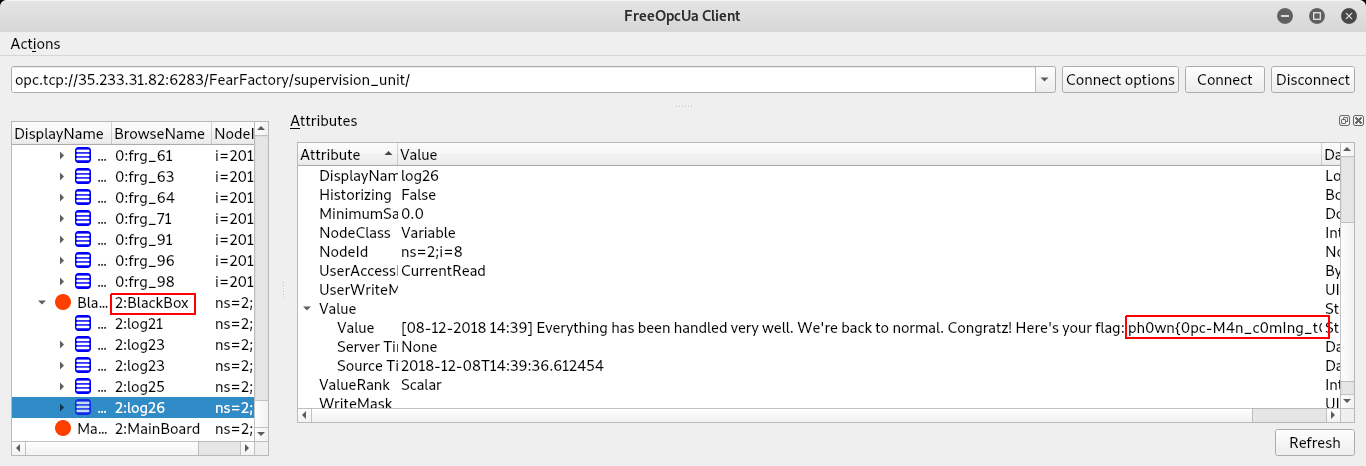
Author:
Clément Notin | @cnotin
Post date: 2018-12-16